In Der Spiegel …
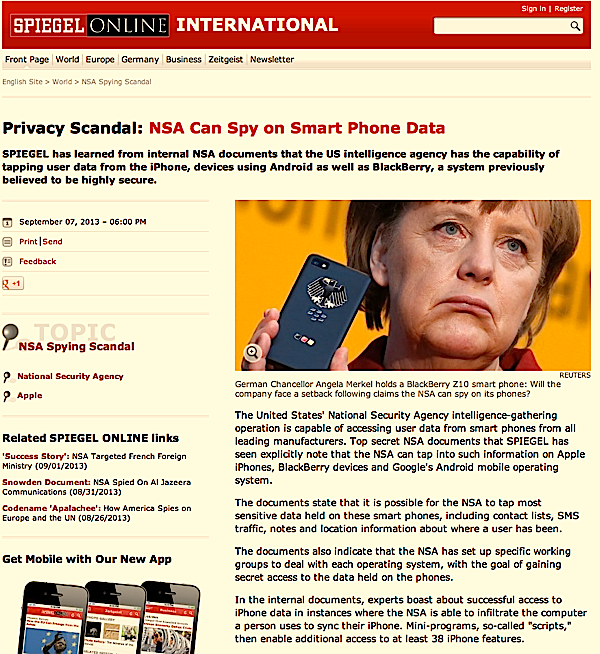
The United States’ National Security Agency intelligence-gathering operation is capable of accessing user data from smart phones from all leading manufacturers. Top secret NSA documents that SPIEGEL has seen explicitly note that the NSA can tap into such information on Apple iPhones, BlackBerry devices and Google’s Android mobile operating system.
The documents state that it is possible for the NSA to tap most sensitive data held on these smart phones, including contact lists, SMS traffic, notes and location information about where a user has been.
see: Privacy Scandal: NSA Can Spy on Smart Phone Data
And special honourable mention for New Zealand in How the N.S.A. Cracked the Web in The New Yorker magazine …
Both the Times and the Guardian write that the N.S.A. and the G.C.H.Q. have “cracked much of the encryption” on the Web. But we don’t know precisely how much: the Times writes that the “full extent of the N.S.A.’s decoding capabilities is known only to a limited group of top analysts from the so-called Five Eyes: the N.S.A. and its counterparts in Britain, Canada, Australia and New Zealand.” But it deploys “custom-built, superfast computers to break codes,” and it works with “technology companies in the United States and abroad to build entry points into their products.”
and Dear NSA, Thanks for Making Us All Insecure in Bloomberg Business Week …
Dear stupid, stupid NSA,
I’ve got to hand it to you: As an agency set up with the task of breaking codes and spying on people, you seem to be doing a pretty sterling job.
You and your counterparts in the U.K., Australia, Canada, and New Zealand (and possibly elsewhere) are able to monitor most of the communications flowing around the world. You appear to have successfully subverted the American Web services that everyone uses, and you’ve used the value and size of the U.S. market to bring all manner of Internet backbone providers and hardware vendors on-side too.
Now we also know that you have—in your own words—some capabilities against the encryption in TLS/SSL, HTTPS, SSH, VPNs, VoIP, WEBMAIL, and other network communication technologies. So even if it takes a fair amount of effort (unlike your indiscriminate data-trawling techniques), that’s basic Internet security out the window then. Nicely done.
We’re still pretty sure that strong cryptography is safe (Edward Snowden said so, and he’s yet to be proven wrong on this stuff), but even there it’s not unreasonable to suspect you can muscle your way in if the situation merits it.
Backlash, anyone?
– P